Configuring settings
Before the Active Directory connection can be activated, certain settings must be configured. It is possible to connect several Active Directories and to import their entries into octoplant.
As a prerequisite, authorization must be carried out via the operating system.
-
Open the Synchronization tab in the menu bar and click on the Account policies button.
-
In the Authorization tab, select either Authorization via operating system or Authorization by operating system and access management and confirm with OK.
To configure the settings for the Active Directory connection, proceed as follows:
-
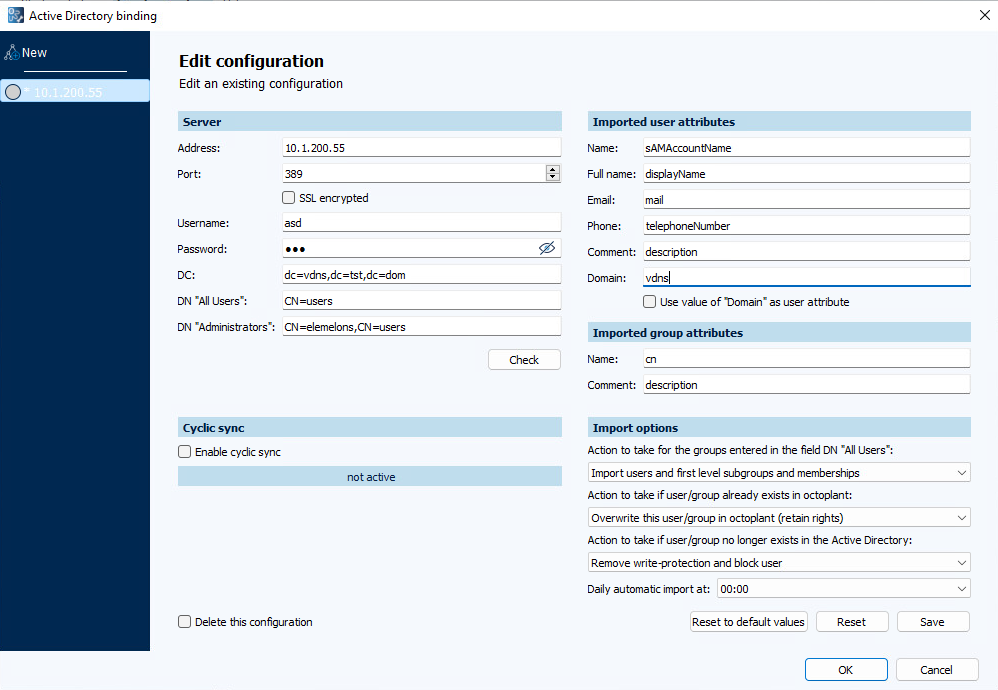
Click on the Configure button in the menu bar. The Active Directory binding dialog is displayed. A new configuration is created directly when it is initially opened. If you want to create an additional configuration while the dialog is open, select the New button in the navigation bar on the left.
-
Make the necessary settings. An example configuration you can see in the screenshot above. The entries are described in detail in the tables below.
-
Select Enable cyclic sync to activate the synchronization with the Active Directory for this configuration.
-
Confirm with Save.
-
The settings of this configuration are saved. To add a new configuration select the New button in the navigation bar, to close the dialog select OK.
 The automatic and manual import from the Active Directory is finally only active, when the Activate button in the menu bar is selected. The Enable cyclic sync checkbox only enables the configuration for being activated afterwards.
The automatic and manual import from the Active Directory is finally only active, when the Activate button in the menu bar is selected. The Enable cyclic sync checkbox only enables the configuration for being activated afterwards.
 When configuring the Active directory connection, data supplied by the IT department, for example, is often copied from an email or a Word document. It can happen that characters are changed or added by the corresponding word processing program. This will be indicated by an error message. To prevent this, we recommend entering the data manually.
When configuring the Active directory connection, data supplied by the IT department, for example, is often copied from an email or a Word document. It can happen that characters are changed or added by the corresponding word processing program. This will be indicated by an error message. To prevent this, we recommend entering the data manually.
Server
 We have implemented automatic authentication for Active Directory. This means that already authenticated credentials will be used if the supplied credentials, username and password, are left empty in the Active Directory binding dialog.
We have implemented automatic authentication for Active Directory. This means that already authenticated credentials will be used if the supplied credentials, username and password, are left empty in the Active Directory binding dialog.
| Element | Description | Example |
|---|---|---|
| Address | Name, IP address or domain of the Active Directory servers If the computer from which you want to connect is not included in the domain of the Active Directory server, a connection will only be possible via the name or IP address of the Active Directory server. If the computer from which you want to connect is not included in the domain of the Active Directory server, a connection will only be possible via the name or IP address of the Active Directory server. |
10.0.201.1 |
| Port | Active directory server port Integer values ranging from 0 to 65535 are possible The default port for encrypted connection is port 636 (default port for unencrypted connection is 389) If a port is already being used for something else, select another one. |
636 |
| SSL encrypted | Encrypted or unencrypted connection to the Active Directory server.
By default, the connection to Active Directory is made using the LDAP protocol. If the SSL Encrypted checkbox is selected, the LDAPS protocol will be used. |
þ SSL encrypted |
| User name | User name for access to the Active Directory Server Format: <User name> or <Domain>\<user name> or <username>@<domain> |
octoplant |
| Password | User name for access to the Active Directory Server masked display |
••••••••• |
| DC | DNS name of the domain Information according to the Active Directory format The parts of a domain name separated by dots are divided into individual sections in the Active directory. Each section is intiated by the prefix DC (= Domain Component). The individual sections are separated from each other by commas ie domain "vdns.tst.dom" is mapped as follows: DC=vdns, DC=tst, DC=dom |
DC=vdns, DC=tst, DC=dom |
| DN "All Users" | Distinguished Name (= DN) of the Active Directory group, within which users (and other groups), that are to be imported, are searched for. Entries corresponding to the Active Directory Format. A distinguished name represents an object in a hierarchical directory. The distinguished name is written from the lower to the higher hierarchy levels. The object itself is introduced by the prefix CN (= Common Name). The individual parts are separated from each other by commas For the group "Club27" in the folder “Users”, the Distinguished Name looks like this: CN=Club27, CN=Users |
CN=Club27, CN=Users |
| DN “Administrators” |
Distinguished Name (= DN) of the Active Directory group, whose users are to be imported into the Administrators group Multiple groups are separated from each other by semicolons. |
CN=Reservoir-Dogs, CN=Users, OU=SecurityGroup.
CN=SECS-Engineering-1,OU=test,OU=2008 R2 AD; CN=SECS-Engineering-2,OU=test 2,OU=2008 R2 AD; ... |
Path specification:
Paths need to be entered in full in the Active Directory Binding dialog. If the path contains special characters, such as "+" (for example, OU=W+D), this special character must be provided with an escape sequence "\" (for example, CN=Reservoir-Dogs, OU=W\+D).
You can use the Check button to test whether the server details are correct.
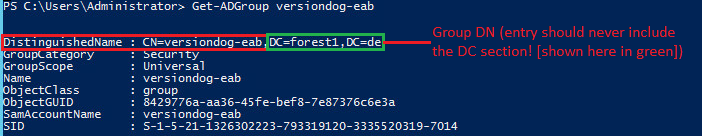
Issuing Distinguished Name of Active Directory Group
In the fields DN "All Users” and DN "Administrators" the distinguished name of an Active Directory group is specified. The distinguished name can be issued via the PowerShell command Get-ADGroup <group name> executed on the Active Directory controller.
Example:
Imported user attributes
| Element | Description | Example |
|---|---|---|
| Name | Attribute from the Active Directory, which is used as user name in octoplant During the import, the name of a user is set according to the value of the attribute from the Active Directory. |
sAMAccountName |
| Full name | Attribute from the Active Directory, which is used as the full name in octoplant During the import, the name of a user is set according to the value of the attribute from the Active Directory |
displayName |
| Attribute from the Active Directory, which is used as the email address in octoplant. During the import, the email address of a user is set according to the value of the attribute from the Active Directory. |
||
| Telephone | Attribute from the Active Directory, which is used as the telephone number in octoplant During the import, the telephone number of a user is set according to the value of the attribute from the Active Directory. |
telephoneNumber |
| Comment | Attribute from the Active Directory, which is used as a comment in octoplant During the import, the comment of a user is set according to the value of the attribute from the Active Directory. |
description |
| Domain |
Domain name or user attribute from the Active Directory If the checkbox Use value of "Domain" as user attribute has been cleared, the NetBIOS name of the domain will be entered. This is the default setting. If the checkbox Use value of "Domain" as user attribute has been selected, any user attribute can be specified from which the domain name can be read or used. 2 Special features: For the userPrincipalName and distinguishedName attributes, the first sub-domain or domain found is used as the domain name in each case. Examples:
Here, the first value after the @ up to the first "." is used as the domain name, in other words, "subdomain". |
Imported group attributes
| Element | Description | Example |
|---|---|---|
| Name: | Attribute from the Active Directory, which is used as user name in octoplant During the import, the name of a group is set according to the value of the attribute from the Active Directory. |
cn |
| Comment: | Attribute from the Active Directory, which is used as group comment octoplant During the import, the comment of a group is set according to the value of the attribute from the Active Directory. |
description |
Import options
| Element | Description |
|---|---|
| Procedure for the groups entered in the DN "All Users" field |
|
| Action to take if user/group already exists in octoplant: |
Program behaviour, if users/groups, that are set to be imported, already exist in octoplant. Options:
|
| Action to take if user/group no longer exists in the Active Directory: |
Program behaviour, if users/groups, that are set to be imported, no longer exist in octoplant. Options:
|
| Daily automatic import at: | Time to start the daily automatic import (selectable are full hours). |
Example configuration:

 By clicking on Rest to default, all entries are undone and the initial state of the configuration dialog is restored.
By clicking on Rest to default, all entries are undone and the initial state of the configuration dialog is restored.
Additional information:
Much of the information required for the Active Directory Binding in octoplant can be found fast and easily with a tool for managing the Active Directory. For example, the Active Directory Explorer from Microsoft is such a tool. If the port is explicitly specified, the SSL connection can also be checked.
Example:
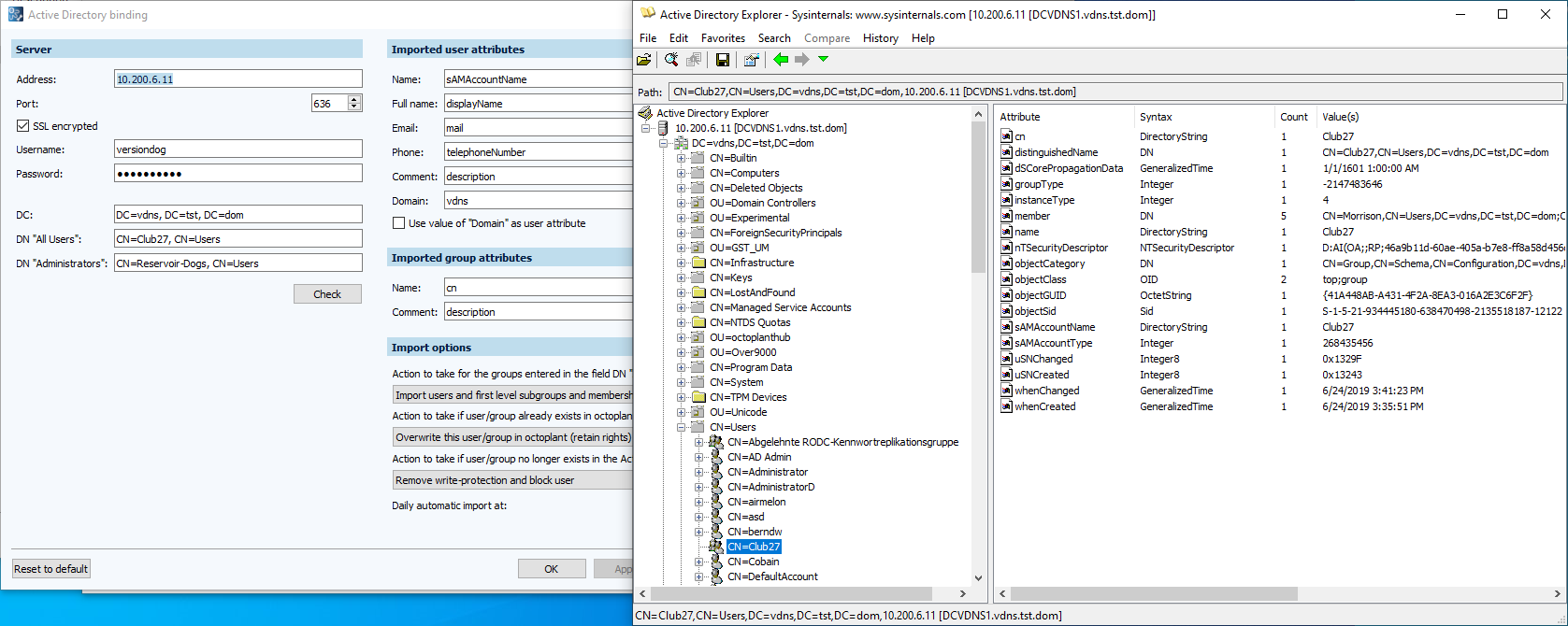
The following screenshot shows the information needed to configure the Active Directory Binding so as to be able to import the group "Club27" from the "Users" folder via Active Directory Explorer. Information relevant to each other can be recognized by the same number.
|
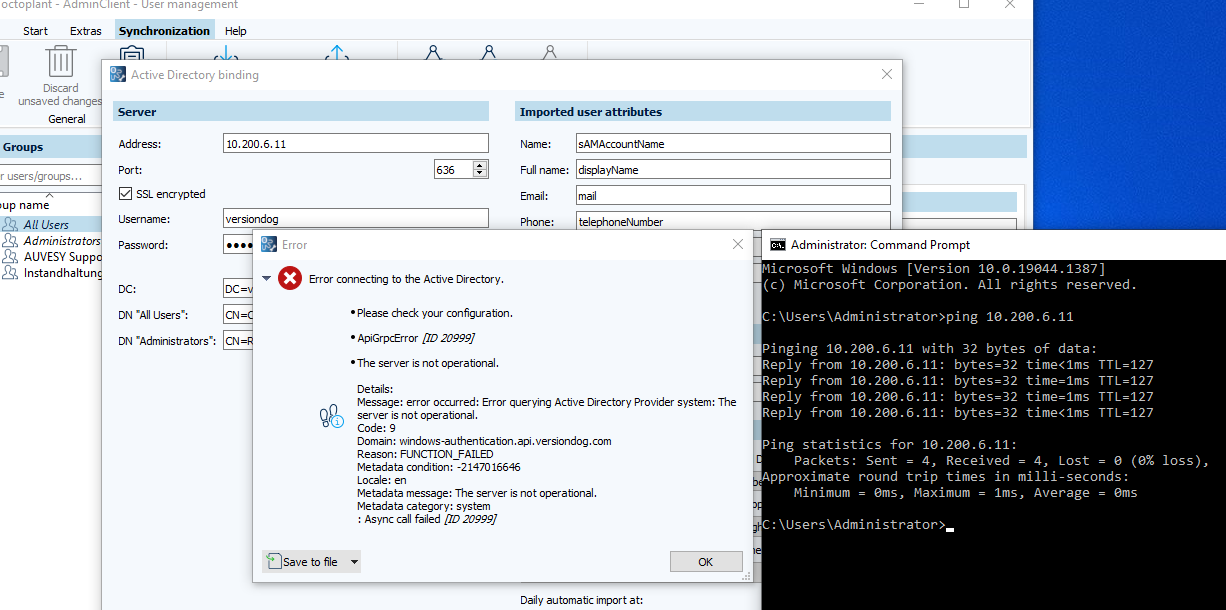
SSL encrypted connection to Active Directory server fails with the following error message. How can I resolve this problem?
Check if the name in the certificate matches the name in the request. In the above example, the IP address was used instead of the computer name "FS-2019" during configuration. Since only the name "FS-2019" is stored in the certificate, the displayed error occurs. To fix the error, specify the computer name "FS-2019" in the Address field.
|
|
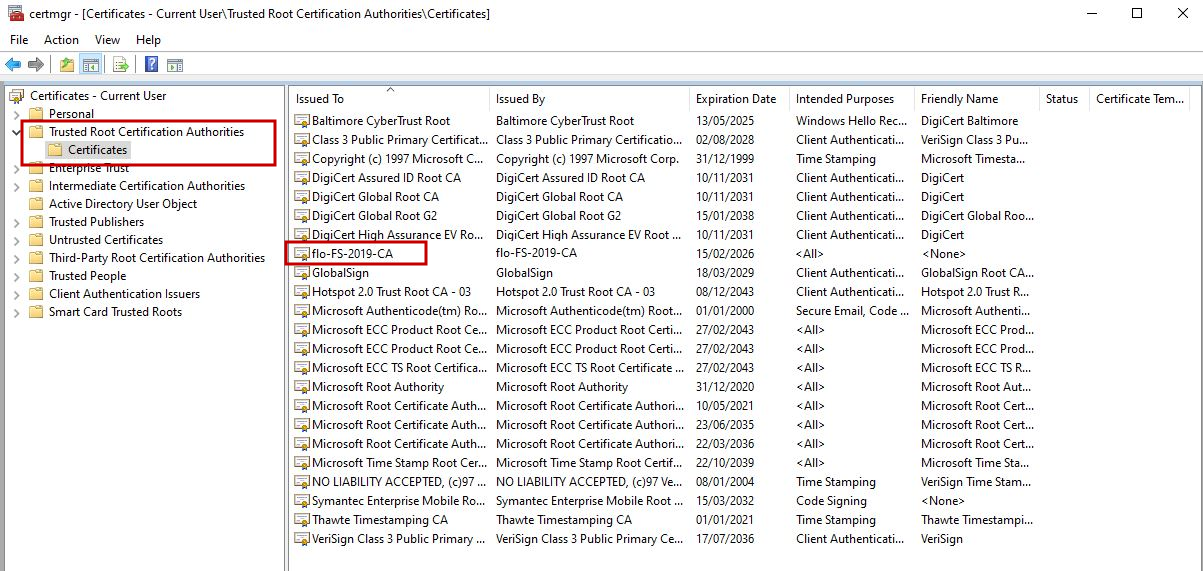
How can I import a certificate on the octoplant server or check its availability?
A root certificate identifies a certification authority (CA). With this root certificate, a CA signs one or more subordinate certificates that sign the SSL certificates of the end users. The root certificate must be imported to the server. To do this, double-click the exported certificate and file it under Trusted root certification authorities.
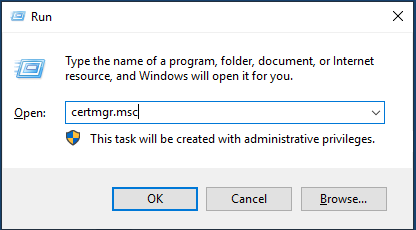
To display the certificate, press Win + R and enter certmgr.msc (or certlm.msc) in the Run dialog.
|